Erin Plante, Senior Director of Investigations at Chainalysis, states, “With the help of law enforcement and leading organizations in the cryptocurrency industry, more than $30 million worth of cryptocurrency stolen by North Korean-linked hackers has been seized.”
Chainalysis aided law enforcement authorities in recovering $30M stolen from Axie Infinity by the Lazarus Group, the perpetrators behind the Ronin Bridge hack.
The Ronin Network was hacked earlier this year when the hackers, now identified as the Lazarus Group, gained access to five out of the nine private keys and used them to approve two transactions: 173.6K Ethereum and 25.5M USDC tokens, resulting in a loss of over $600M for Ronin Network.
1/ Today at #AxieCon, Senior Director of Investigations @eeplante joins the @AxieInfinity team to deliver good news…
— Chainalysis (@chainalysis) September 8, 2022
Lazarus Group leveraged the stolen funds to over 12K different addresses to hide their tracks.
Chainalysis detailed the process used by Lazarus Group to launder funds: the hackers would first send their stolen assets to intermediary wallets before mixing them through Tornado Cash. Subsequently, they would swap the laundered Ethereum tokens for BTC, send the Bitcoin assets again through Tornado Cash and cash out the profits at crypto exchanges.
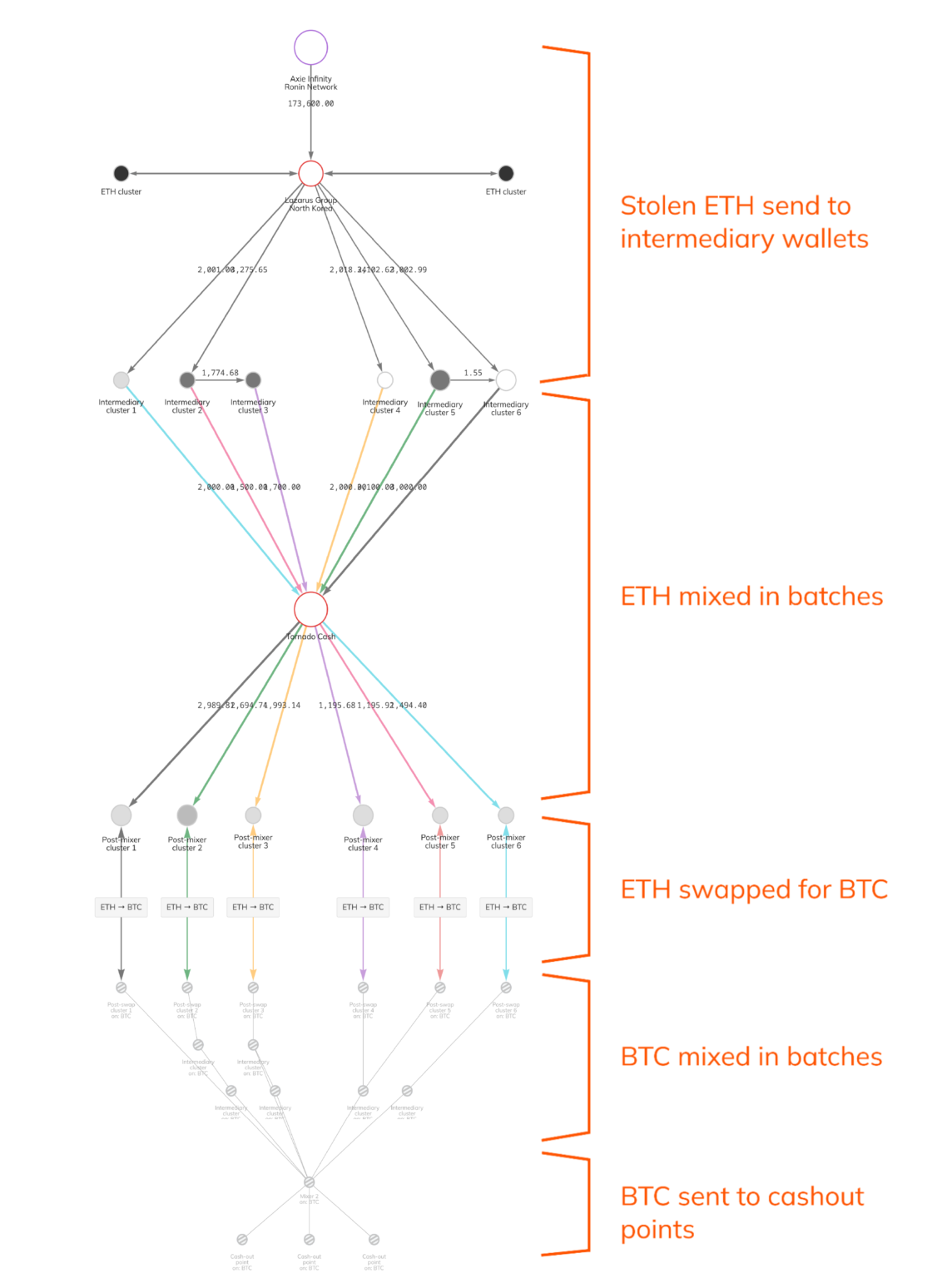
However, Lazarus Group stopped utilizing coin mixing tools after the US Treasury sanctioned Tornado Cash, instead switching to cross-chain bridges to launder their funds.
Chainalysis noted that the fund movements across cross-chain bridges were easy to track using its tools, thanks to the transparency of blockchain transactions. The firm revealed that in one instance, the perpetrators bridged the stolen Ethereum funds to the BNB chain and swapped them into USDD before bridging them to the BitTorrent Chain.
As a result, Chainalysis could recover 10% of the funds stolen in the Ronin Bridge exploit by collaborating with law enforcement authorities, with Erin Plante adding,
“This marks the first time ever that cryptocurrency stolen by a North Korean hacking group has been seized, and we’re confident it won’t be the last.“
We’re glad you read to this point!
Every week, we publish an email newsletter highlighting all the juicy stories we covered in the crypto space, bringing all the major happenings to your doorstep.
So, if you want to have top stories delivered to your email inbox every week, subscribe to our newsletter!